Urgent Security Update: Wannacry Ransomware
On Friday May 12th, a new ransomware threat was discovered, named “Wannacry”. Ransomware has been a constant threat for a couple years, but fortunately mitigated very quickly. Wannacry in particular has been a very serious threat, taking advantage of a Windows vulnerability that has only been very recently patched. There have already been several large companies affected by it, such as FedEx, various financial institutions, hospitals and schools, in just a few days.
What is Ransomware?
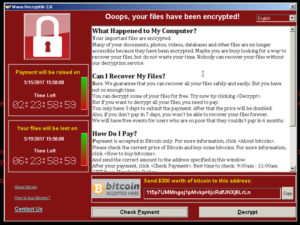
Ransomware works by finding a vulnerability in a system then running code to encrypt all accessible files. Once the encryption is complete, it send any keys necessary to be able to unencrypt your files to the ransomer, deletes them from your system, then a window appears as pictured below.
What makes “Wannacry” different?
Wannacry takes advantage of an exploit in SMB (server message block). SMB is how files are accessible on computers in a windows network. Wannacry is also a worm, which means it will scan for computers that it has the ability to infect. It will originally infect a computer from spam email, another infected computer on the local network, or from the internet over SMB ports 139 or 445. Once it finds a system it can infect, it will remotely execute its code, which consists of copying what it needs, then running without the user knowing. While encrypting files on the system, it is also actively scanning the network for any other system that has the same vulnerability, thus continuing the cycle. Network drives and attached USB hard drives or thumb drives are also at risk.
What if I’m already infected?
Unfortunately, unless you have a good backup, there is nothing that can be done. The only way an encrypted file in this fashion can be made readable again is to unencrypt it with the key used to encrypt them. Ransomware like Wannacry will send the key to the attackers then remove it from the system entirely. Even if the attackers are paid the ransom, there is no guarantee that they will send the key. You would have a better chance of winning the lottery than getting the key. DO NOT PAY THE RANSOM. This only furthers the desire for people to make these malicious programs. Bitcoin is also an untraceable anonymous currency, so there is no way to track down where the payment goes. You can read more about bitcoin here: https://bitcoin.org/en/faq
What can I do to protect myself?
The SMB vulnerability, as well as a couple others, were actually patched on March 14th 2017 by Microsoft. Many people and organizations tend to hold off on installing the most recent updates, whether it stem from application compatibility, lack of time and staffing, or internet bandwidth concerns. Windows systems that are completely up to date will not be affected by the current code of Wannacry. PLEASE UPDATE ALL WINDOWS SYSTEMS FULLY, IMMEDIATELY. Hardware firewalls on the perimeter of the network (internet facing side) will also help prevent the attack hitting the local network by blocking the 2 ports that Wannacry spreads. As always, backups are extremely important. If a computer is affected, but has a backup that isnt directly accessible from the infected computer, your data up to the point of backup will be safe. An indirectly accessible location would be something like a NAS (network attached storage), a removable hard drive that doesn’t stay connected, or a cloud backup. Removable hard drives that stay connected all the time run the risk of being encrypted.
Please contact us if you need assistance in making sure your systems are secure and backed up. We can provide the necessary software and service to ensure risks like this are no longer a major concern.
For more detailed information about Wannacry, check out this article written by Talos, Cisco’s security divison: http://blog.talosintelligence.com/2017/05/wannacry.html


Leave a Reply
Want to join the discussion?Feel free to contribute!